Understanding the steps devices go through when connecting to the Wireless network will help clarifying what is being captured with the protocol analyzer.
In this blog will talk about all the steps of mobile device connecting to the WLAN. below is outlined on a high level steps 1 to 20 that cover the process for accessing a Wireless Lan.
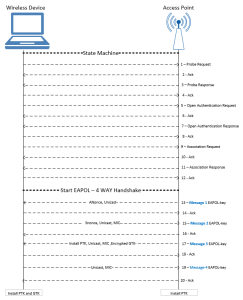
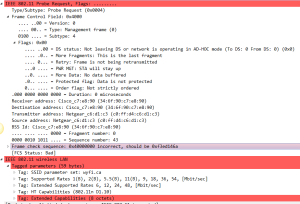
1: Probe Request
Sent by a mobile device to discover WLAN networks close by. The Station will advertise its supported rate, Extended supported data rates, HT capabilities and SSID as shown below with more details
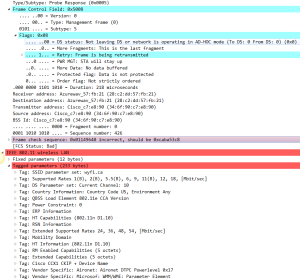
3: Probe Response
The Access point receives the probe request and responds to the sending station with its capabilities.
The AP tagged parameters will include: SSID, Supported data rates and extended supported data rates, HT capabilities and other details as shown below.
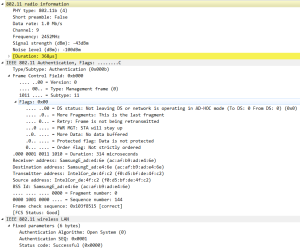
5: Authentication Request
Once the mobile device discover the WLAN it will start joining the WLAN with an Authentication request sent by the AP to the device as part of the open system authentication:
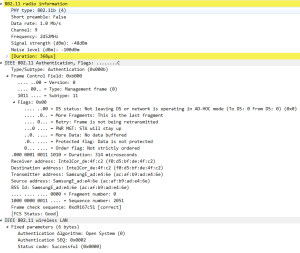
7: Authentication response
The mobile device response to the authentication request. note the ” Authentication SEQ” and SA (Source address) to determine the initiator.
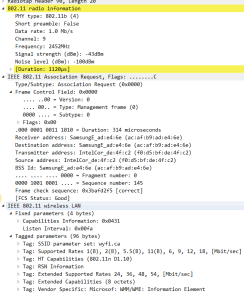
9: Association request
After the mobile device determines which Access Point to connect to, it will send and association request to that Access point.
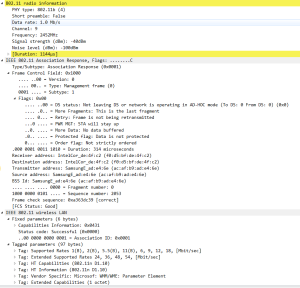
11: Association Response
The AP will receive the request from the mobile device and if the Elments in the association request match the capabilities of the AP, the Association ID (AID) is created by the AP and respond with an associate response frame to the mobile device.
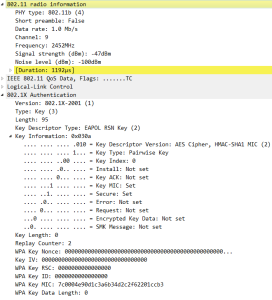
EAP over LAN, 4 way handshake
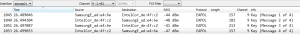
13: 4 WAY Handshake (EAPOL-key) Message 1
Access point sends EAPOL message with ANonce to the mobile device to generate PTK.It has PMK, Snonce and its own MAC address. Once it receives ANonce from access point it has all the inputs to create the PTK.
PTK = PRF (PMK + Anonce + SNonce + Mac (AA)+ Mac (SA))
Mac address SamsungE_ad:e4:6e is source address or mac address of the access point who is sending first EAPOL message to the device and IntelCor_de:4f:c2 is Mac address of the mobile device. In this message access point sending ANonce to the client device.
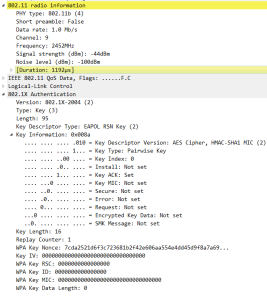
15: 4 WAY Handshake (EAPOL-key) Message 2
Mobile device responds with SNonce to the AP after creating its PTK, the AP then will create the PTK. Message 2 sent by the mobile device with MIC (message integrity check) to insure that the message was not corrupted.
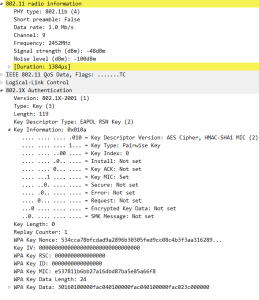
17: 4 WAY Handshake (EAPOL-key) Message 3
Sent from the Access Point to the mobile device with the GTK ( GTK is created by the Access Point.
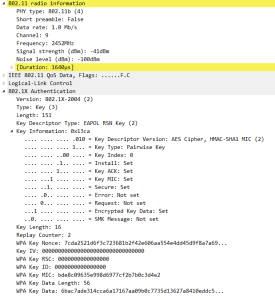
19: 4 WAY Handshake (EAPOL-key) Message 4
The last key is sent by the client to the AP to confirm that the keys have been installed.
once the 4 way handshake is completed successfully, the traffic between the AP and mobile device will be encrypted with the GTK ( Unicast and multicast traffic will be encrypted)
